What is a cloud server?
A cloud server is a computer server that has been virtualized, making its resources accessible to users remotely over a network. Cloud-based servers are designed to perform the same tasks as conventional physical (and virtual) servers that are housed in a nearby data center, support the same operating systems (OSes) and applications, and offer a comparable level of performance. Virtual servers, virtual private servers, and virtual platforms are terms frequently used to describe cloud servers.
There are many cloud server providers that offer a range of cloud computing services, including infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS). Some of the most well-known cloud server providers include:
- Amazon Web Services (AWS)
- Microsoft Azure
- Google Cloud Platform
- IBM Cloud
- Oracle Cloud
- Alibaba Cloud
- Rackspace
- DigitalOcean
- Vultr
- Linode
- Upcloud
These companies provide a variety of services, such as virtual machines, storage, networking, analytics, machine learning, and others. Additionally, they provide a variety of pricing options, such as pay-as-you-go, on-demand, and reserved pricing. It's crucial to thoroughly compare the available choices and pick the one that best suits your requirements and financial constraints.
Select the provider that best meets your needs, register with them using a credit card, sign in to your dashboard, and create your machine. Some platforms may allow you to provide a custom root password; if not, they will likely assign you a random password that you can later change.
I created the server for the demonstration in accordance with the following specifications: 2 CPU, 2 GB RAM, and 50 GB of storage
After you have successfully set up a cloud server, there are a few things you should do on your new Linux system to get it ready to go. This includes updating your system, setting the time zone, configuring a custom hostname, adding a limited user, hardening SSH to prevent unauthorized access, and setting up a firewall. These steps ensure your server is up to date, secure, and ready for use.
Obtain the IP address from the machine's specifications and connect to the server using ssh from your local machine. I use my debian desktop's terminal application, but you can use the same method on any linux-based operating system, or you can use the PUTTY terminal/telnet client application on a Windows computer.
ssh root@172.16.26.165
Perform System Updates
The most important security measure you can take for any operating system is to update it often. Software updates range from critical vulnerability patches to minor bug fixes, and many software vulnerabilities are actually patched by the time they become public. Updating also provides you with the latest software versions available for your distribution.
For, Debian and Ubuntu
apt update && apt upgrade
Set the Timezone
All new servers are set to UTC time by default. However, you may prefer the time zone in which you live, so log file timestamps are relative to your local time.
Both Ubuntu and Debian come with a more friendly tool called tzdata, outlined below.
Open the tzdata tool.
dpkg-reconfigure tzdata
Select the continent of your choice using the arrow keys, and then press Enter.
Select your region using the arrow keys, and then press Enter.
Check the Time
Use the date command to view the current date and time according to your server.
Configure a Custom Hostname
A hostname is used to identify your cloud server using an easy-to-remember name.
To see the current Hostname, run the below command
Run the command below to view the current hostname.
hostnamectl
Replace current hostname with one of your choice.
hostnamectl set-hostname koha.shcollege.ac.in
Update your system’s hosts file.
The hosts file creates static associations between IP addresses and hostnames or domains, which the system prioritizes before DNS for name resolution.
Open the hosts file in a text editor, such as Nano.
nano /etc/hosts
Add a line for your server’s public IP address.
Add a Limited User Account
Up until now, you've logged into your cloud server as the root user, who has full access and can run any command, even ones that could accidentally break your server. I recommend creating a limited user account and using that at all times. Admin tasks will be done with the help of sudo, which temporarily gives your limited user more rights so you can manage your server.
Note
Not all Linux distributions include sudo on the system by default, fortunately Debian/Ubuntu has it, if not install it
apt install sudo
Ubuntu and Debian
Create the user, replacing mahesh with your desired username. You’ll then be asked to assign the user a password.
adduser mahesh
Add the user to the sudo group so you’ll have administrative privileges:
adduser mahesh sudo
Log in as the New User
After creating your limited user, disconnect from your cloud server:
exit
Log back in as your new user. Change mahesh to your username, and the example IP address to the IP address of your instance:
ssh mahesh@172.16.26.165
Now you can administer your cloud server from your new user account instead of root. Nearly all superuser commands can be executed with sudo
Harden SSH Access
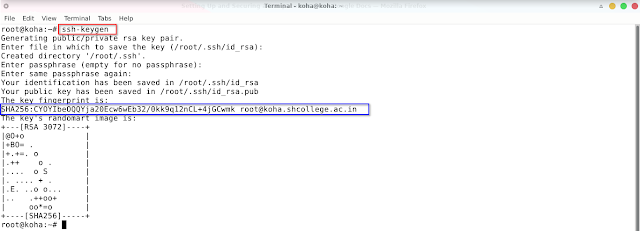
By default, password authentication is used to connect to your cloud server via SSH. A cryptographic key-pair is more secure because a private key takes the place of a password, which is generally much more difficult to decrypt by brute-force attack. In this section, we'll create a key-pair and set up our system so that SSH logins do not require passwords.
This is done on your local computer, not your cloud server, and will create a 4096-bit RSA key-pair. During creation, you will be given the option to encrypt the private key with a passphrase. This means that it cannot be used without entering the passphrase, unless you save it to your local desktop’s keychain manager. We suggest you use the key-pair with a passphrase, but you can leave this field blank if you don’t want to use one.
On Linux
Caution
If you’ve already created an RSA key-pair, this command will overwrite it, potentially locking you out of other systems. If you’ve already created a key-pair, skip this step. To check for existing keys, run ls ~/.ssh/id_rsa*.
ssh-keygen
Press Enter to use the default names id_rsa and id_rsa.pub before entering your passphrase. On Linux, these files will be saved in the /home/your_username/.ssh directory.
To check
ls -l ~/.ssh
Upload the public key to your Compute instance. Replace example_user with the name of the user you plan to administer the server as, and 172.16.26.165 with your instance’s IP address.
Linux
From your local computer:
ssh-copy-id -i ~/.ssh/id_rsa.pub mahesh@172.16.26.165
These commands add an extra layer of security because they prevent other users from accessing the public key directory and the file itself.
Now exit and log back into your cloud server. If you specified a passphrase for your private key, you’ll need to enter it.
Caution
Better keep a copy of your SSH key, both the private and public key, somewhere else at all times.
SSH Daemon Options
Use a Linux text editor like nano or vim to open the SSH configuration file on your cloud server:
sudo vim /etc/ssh/sshd_config
Disallow root logins over SSH: This requires all SSH connections to be made by non-root users. Once a limited user account is connected, administrative privileges are accessible either by using sudo or by changing to a root shell using su.
pair for every device.
Disable SSH password authentication: This requires all users connecting via SSH to use key authentication. Depending on the Linux distribution, the line PasswordAuthentication may need to be added, or uncommented by removing the leading #.
Note
You may want to leave password authentication enabled if you connect to your s from many different computers. This will allow you to authenticate with a password instead of generating and uploading a key-pair for every device.
Listen to only one internet protocol: The SSH daemon listens for incoming connections over both IPv4 and IPv6 by default. Unless you need to SSH into your server using both protocols, disable whichever you do not need. This does not disable the protocol system-wide; it is only for the SSH daemon. Depending on the Linux distribution, the line AddressFamily may need to be added, or uncommented by removing the leading #
Use the option:
AddressFamily inet to listen only on IPv4.
AddressFamily inet6 to listen only on IPv6
Restart the SSH service to load the new configuration.
sudo systemctl restart sshd
Setting Up a Firewall with UFW
By default, both Debian and Ubuntu come with a firewall configuration tool called UFW (Uncomplicated Firewall). UFW is a user-friendly front-end for managing iptables firewall rules and its main goal is to make managing iptables easier or as the name says uncomplicated.
Install UFW
sudo apt install ufw
Check UFW Status
Once the installation is completed you can check the status of UFW with the following command:
sudo ufw status verbose
or
sudo systemctl status ufw
Allow SSH Connections
Before enabling the UFW firewall we need to add a rule which will allow incoming SSH connections. If you’re connecting to your server from a remote location, which is almost always the case and you enable the UFW firewall before explicitly allow incoming SSH connections you will no longer be able to connect to your server.
To configure your UFW firewall to allow incoming SSH connections, type the following command:
sudo ufw allow ssh
or
sudo ufw allow 22/tcp
Enable UFW
Now that your UFW firewall is configured to allow incoming SSH connections, we can enable it by typing:
sudo ufw enable
sudo systemctl start ufw
(You will be warned that enabling the firewall may disrupt existing ssh connections, just type y and hit Enter)
Allow connections on other ports
Depending on the applications that run on your server and your specific needs you’ll also need to allow incoming access to some other ports.
Below we will show you a few examples on how to allow incoming connections to some of the most common services
Open port 80 - HTTP
HTTP connections can be allowed with the following command:
sudo ufw allow http
instead of http you can use the port number, 80:
sudo ufw allow 80/tcp
Open port 443 - HTTPS
HTTP connections can be allowed with the following command:
sudo ufw allow https
To achieve the same instead of https profile you can use the port number, 443:
sudo ufw allow 443/tcp
Open port 8080
If you run Tomcat or any other application that listens on port 8080 to allow incoming connections type:
sudo ufw allow 8080/tcp
sudo ufw allow 8002/tcp
Delete UFW Rules
There are two different ways to delete UFW rules, by rule number and by specifying the actual rule.
Deleting UFW rules by rule number is easier especially if you are new to UFW. To delete a rule by a rule number first you need to find the number of the rule you want to delete, you can do that with the following command:
sudo ufw status numbered
To delete rule number 3, the rule that allows connections to port 8080, use the following command:
sudo ufw delete 3
The second method is to delete a rule by specifying the actual rule, for example if you added a rule to open port 8080 you can delete it with:
sudo ufw delete allow 8080
Disable UFW
If for any reason you want to stop UFW and deactivate all the rules you can use:
sudo ufw disable
Later if you want to re-enable UTF and activate all rules just type:
sudo ufw enable
Reset UFW
Resetting UFW will disable UFW, and delete all active rules. This is helpful if you want to revert all of your changes and start fresh.
To reset UFW simply type in the following command:
sudo ufw reset
Use Fail2Ban for SSH Login Protection
Fail2Ban is an application that stops IP addresses from logging into your server after too many failed login attempts. Since legitimate logins usually don't take more than three tries to work (and with SSH keys, no more than one), a server that keeps getting bombarded with failed logins is probably being used to try to get into it illegally.
Ensure your system is up-to-date.
sudo apt update && sudo apt upgrade -y
Install Fail2ban:
sudo apt install fail2ban
The service automatically starts.
(Optional) If you would like email support, install Sendmail.
sudo apt install sendmail-bin sendmail
Go to the fail2ban directory
cd /etc/fail2ban
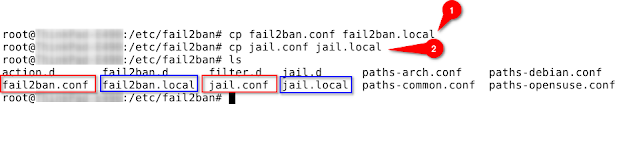
Here you can see two files: fail2ban.conf and jail.conf. These should be copied to another name, and we will modify a few things in the copied files. The reason we do not modify the original files is that they may be overwritten when the server/fail2ban package is updated.
sudo cp fail2ban.conf fail2ban.local
sudo cp jail.conf jail.local
Fail2ban jail.local Configurations
To become more familiar with Fail2ban’s available settings, open your jail.local file and browse the available configurations and set your times and save the file.
sudo vim jail.local
Restart fail2ban service
sudo systemctl restart fail2ban
sudo fail2ban-client status
Create a Swap file
Referenece: